Did you know that Office 365 has a robust auditing feature that allows you to search for all kinds of user activity? You can check to see if a User was added or removed from Office 365 (and who did it), see who activated a process or plug-in in Dynamics 365, and so much more. From these logs, it’s possible to see basic activities from the following apps:
Dynamics 365
Microsoft Flow
Microsoft Stream
Power BI
eDiscovery
Directory Administration
Role Administration
Application Administration
Azure AD Group Administration
User Administration
Sway
Exchange Mailbox
Site Administration
Site Permissions
Synchronization
Sharing and Access Requests
Folders
File and Page
I believe the bottom three activity types refer to SharePoint and OneDrive. To learn more about Audit Logs in Office 365, check out this article from Microsoft.
To access and search these logs, log into Portal.office.com.
Select Security & Compliance:

If you don’t see the Security & Compliance icon, select “Explore all your apps” and search for it.
If you still don’t see it, you may not have access; request your administrator to give you the Global Admin role.
After navigating to the Security & Compliance app, click on “Search & investigate”, then “Audit log search”:
From this screen, you can enter search criteria based on Activities (this is a massive drop-down list organized by Application), Start & End date of activity, specific Users, and File/Folder/Site (you only need part of a name or URL). Results are displayed to the right and include details like IP Address and a general description of the activity:
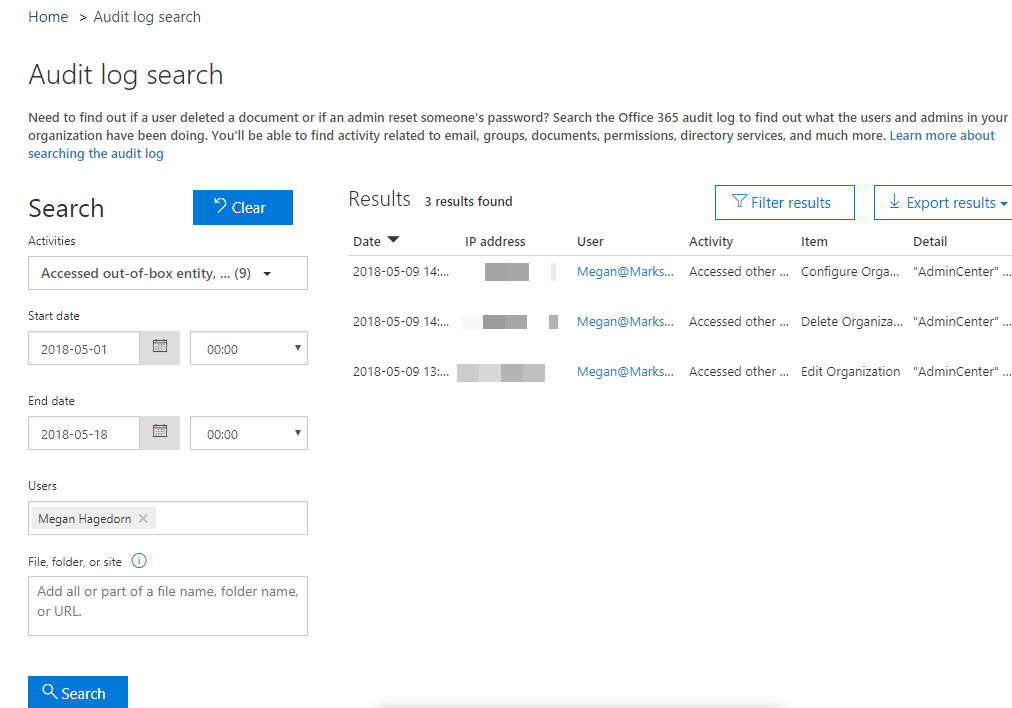
In the example above, I had deleted an instance of Dynamics and created a new one, which you can see from the “Item” Column. You also export and filter these results.

